In this blog we ‘ll learn about hashicorp vault spring boot integration. If you haven’t heard about hashicorp vault before no need to worry. We ‘ll explain hashicorp vault in detail. We ‘ll cover from installation of hashivorp vault till store secret configuration data into hashicorp vault.
Topics
- What is Hashicorp Vault
- Install Hashicorp Vault in Windows system
- Store secret data into Hashicorp Vault
- Basic commands for Hashicorp Vault
- Hashicorp Vault spring boot integration
What is Hashicorp Vault?
Hashicorp vault is an open source secret management system. In simple terms we can say hashicorp vault is used to store sensitive data. It help us to store and manage sensitive data like Database credentials, API Keys details, Certificate etc.
When we work on any project there are many configuration that are sensitive and we don’t want to store it in our configurations file. So to overcome this issue hashicorp come into the picture. Hashicorp help to store all secret data into one single location instead of configuring them in our properties filles.
Hashicorp vault also provides features like Policies and Authentication method to allow control over who can access these secrets.
Install Hashicorp Vault in Windows system
Installing hashicorp vault in windows system is very easy. You just have to follow some steps. If you are using any other operating system you can follow this link to download hashicorp vault Insall Hashicorp
Steps to follow for window system
- Go to Hashicorp Vault site Hashicorp
- Click on binary downloads AMD64 version
- After download completed you ‘ll get a zip file in your download folder extract that zip
- In Extracted folder you ‘ll see vault application file
- Copy the path of this folder. Go to the command prompt and go till the path pf extracted vault folder
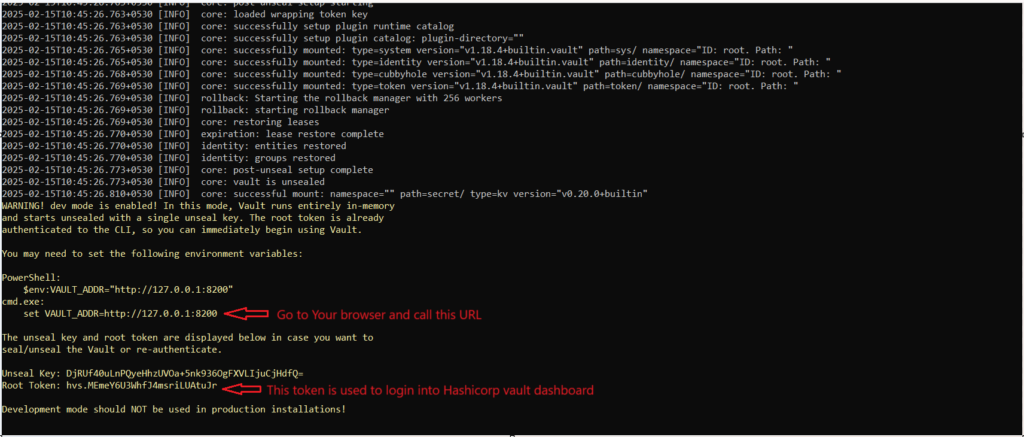
- Run the command vault.exe server -dev
- After server start you ‘ll see some variable like VAULT_ADDR and Root Token
- VAULT_ADDR is the URL address where your vault server is running. Go to your browser and call this URL
- Root Token is the token that is used to login into your vault server.
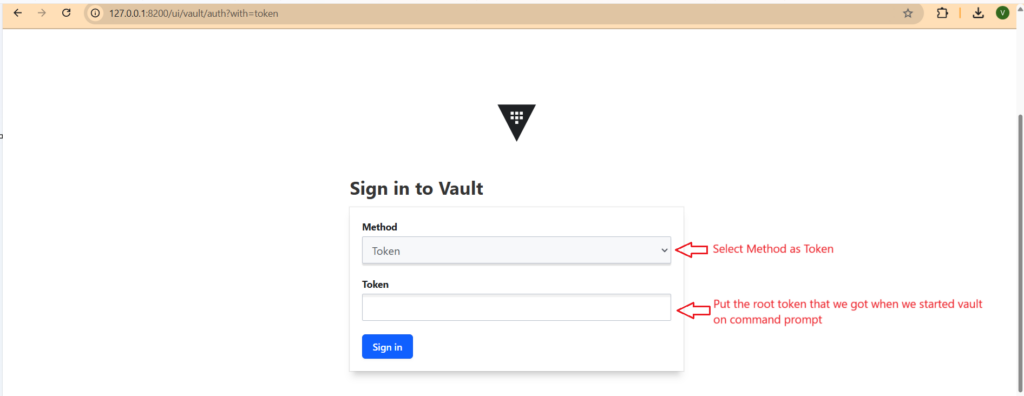
- Once your Vault dashboard open after calling VAULT_ADDR URL. You ‘ll see a login screen
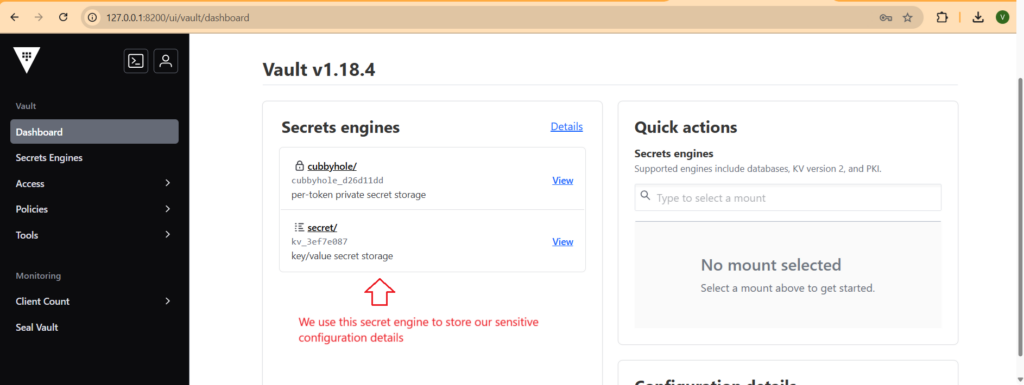
- Select method as Token and on password put the Root Token value. After successfully login you can see the hashicorp vault dashboard. Just play with this dashboard and try to understand functionallity.
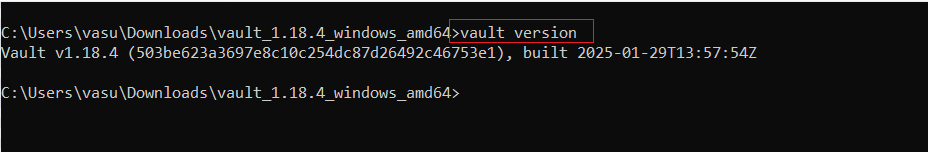
- Once all done you can checkout which version of vault you are using. Open command prompt on same location where vault application file present and run the command vault version
Note: We are running the command on command prompt at vault installation folder location. If you want to run this commands from any location make sure you have set the vault in your system environment variables.
Follow the complete screen shots of the steps described above. This ‘ll help you in your installation process.
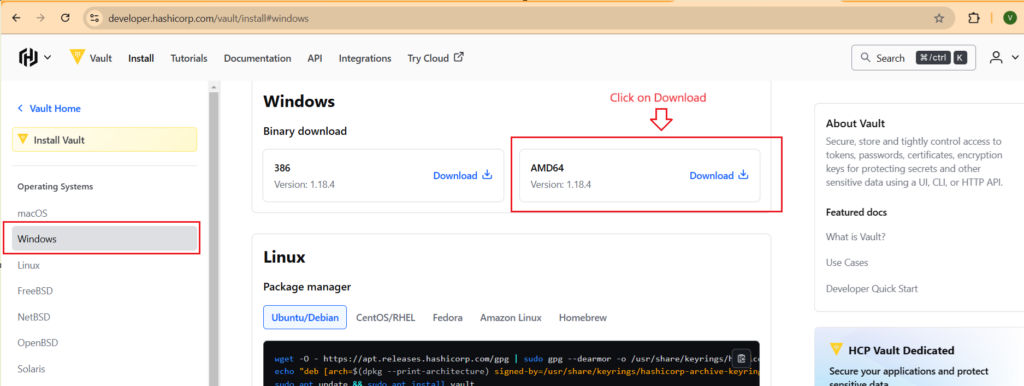
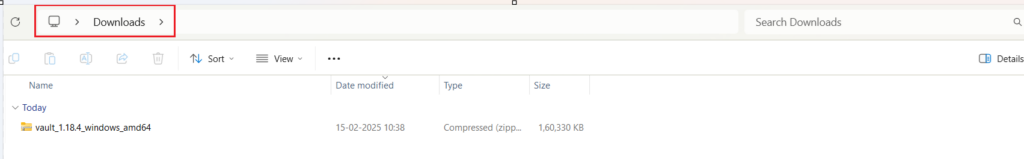

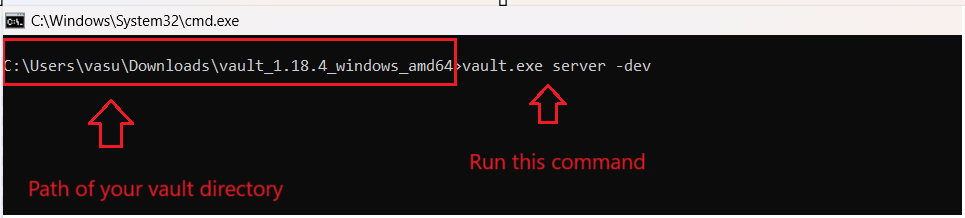
We have successfully installed hashicorp vault in our window systems. If you are using any other operating system, i am hoping that you also done with the installation.
Store Secret in Hashicorp Vault
To store secret in hashicorp vault we have to follow the below steps:
Use hashicorp vault dashboard
- Login to hasicorp vault dasboard
- Click on Secrets Engines
- Click on secret
- Click on Create Secret
- Give name of your choice in Path for the secret
- Enter your sensitive data in key-value format
- If you need to more click on Add button and add more data
- click on save button



Basic commands for hashicorp vault
So let’s start with some basic command of hashicorp. But before jump into that i want to highlight one point. After your vault server start when you try to run vault commands you ‘ll get the below error.
Error listing secrets engines: Get "https://127.0.0.1:8200/v1/sys/mounts": http: server gave HTTP response to HTTPS clientCode language: JavaScript (javascript)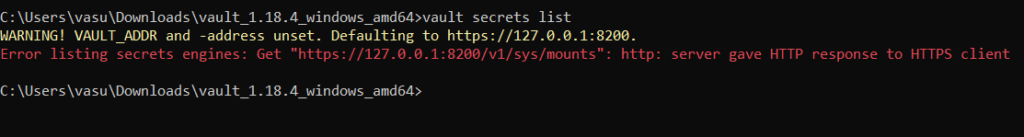
To resolve this we have to set the VAULT_ADDR environment variable. To set this open your command prompt and run the below command.
set VAULT_ADDR=http://127.0.0.1:8200Code language: JavaScript (javascript)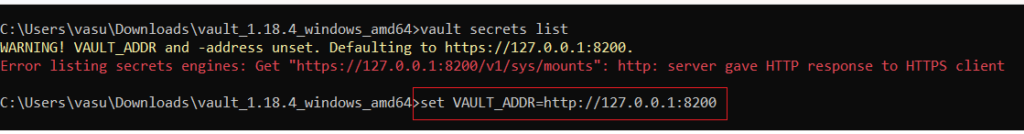
After setting this variable you are good to go. Just try some basic commands of hashicorp vault
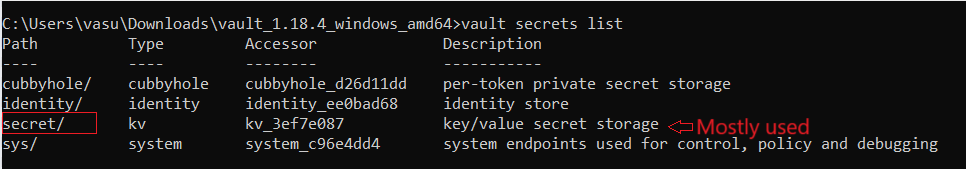
vault secrets list
This command is use to display the secret lists that are present in hashicorp vault. These are the list where we can store our secret. Generally we use secret list to store our sensitive information.
vault kv get secret/vasu-secret-configuration
vault kv get secret command is used to get the details of all secret data that we stored. If you remember in above steps, we have created some secret inside vasu-secret-configuration path using vault dashboard.
If you want to see all the secrets inside that path you have to run below command:
vault kv get secret/vasu-secret-configurationCode language: JavaScript (javascript)
Suppose if we need above response in json formate. Then we have to add the -format=json attribute in above command
vault kv get -format=json secret/vasu-secret-configurationCode language: JavaScript (javascript)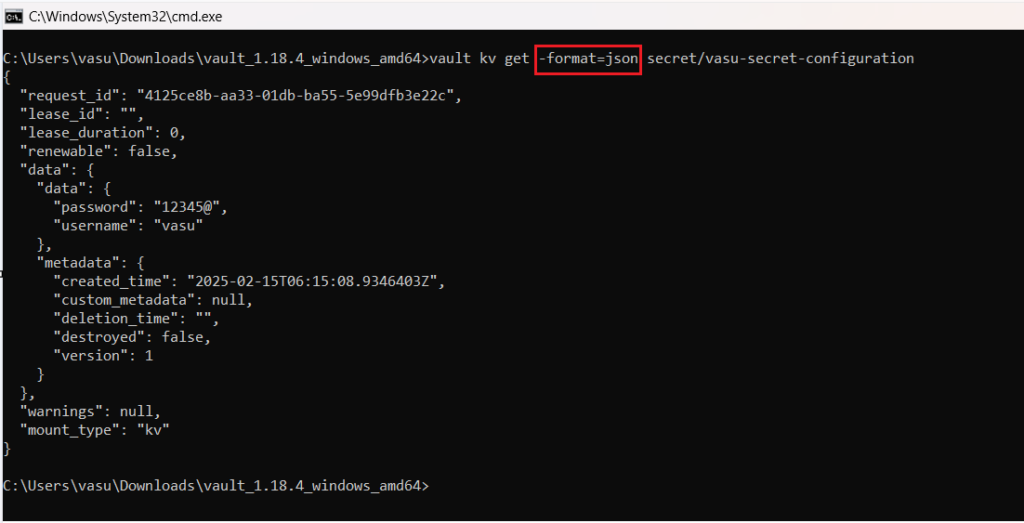
If we need only specific key secret value then we use -field attribute. For example if i need only username value then our command ‘ll be
vault kv get -field=username secret/vasu-secret-configurationCode language: JavaScript (javascript)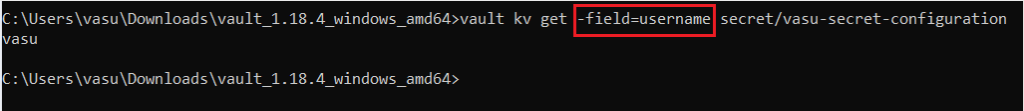
Hashicorp Vault spring boot integration
Now come to final and most interesting part hashicorp vault spring boot integration. This integration is used because we don’t want to save any sensitive data in our application.properties or any other configuration file.
We are using spring boot 3.4.2 along with java 17 version for this example.
For hashicorp vault spring boot integration we have to follow below steps:
- Add vault dependency in our pom.xml file
- Add vault configuration in bootstrap.propertis file
- Access the vault configuration in spring boot application is same as like we use to access any property from application.properties file. We ‘ll use the @value annotation to fetch the value.
Note: As you see in point 2 we are saying that we have to define vault configuration in bootstrap.properties file not in application.properties file. See the reason below:
Why we use bootstrap.properties file for vault configuration
When we work with vault we must use bootstrp.properties file not application.properties. Because application.properties file is load after the spring context start. Due to this reason vault value won’t be available for dependency injection at startup.
We know that bootstrap.properties file loads before the application.properties. So when we work with vault make sure you define vault configuration in bootstrap.propertis, so your vault value would be available for dependency injection at application startup time.
Now Let’s follow the steps for integration:
Project Structure:
Add vault dependency in our pom.xml file
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-vault-config</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-bootstrap</artifactId>
</dependency>Code language: HTML, XML (xml)Add vault configuration in bootstrap.propertis file
# Vault configuration
spring.cloud.vault.uri=http://127.0.0.1:8200
spring.cloud.vault.authentication=token
spring.cloud.vault.token=hvs.9mwLImfMqm6graR2uoNHBnqi
spring.cloud.vault.kv.backend=secret
spring.cloud.vault.kv.default-context=vasu-secret-configuration
# Debug logging
logging.level.org.springframework.cloud.vault=DEBUG
logging.level.org.springframework.vault=DEBUGCode language: PHP (php)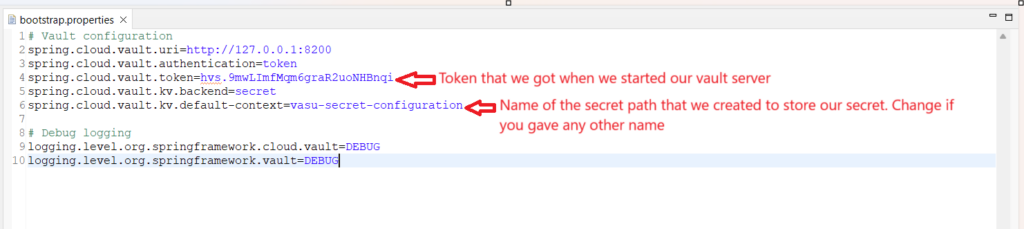
Create a controller class and fetch the value that we define in vault.
package com.javadream.SpringbootWithHashicorpVAult.controller;
import org.springframework.beans.factory.annotation.Value;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RestController;
@RestController
public class VaultController {
@Value("${username}")
private String username;
@Value("${password}")
private String password;
@GetMapping("/fetchFromVault")
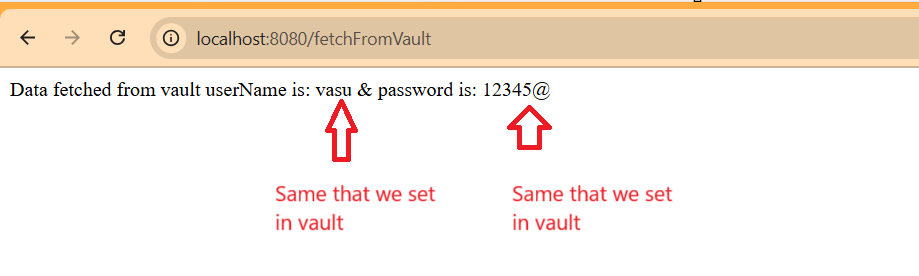
public String fetchVaultSecret() {
return "Data fetched from vault userName is: " + username + " & password is: "+ password;
}
}
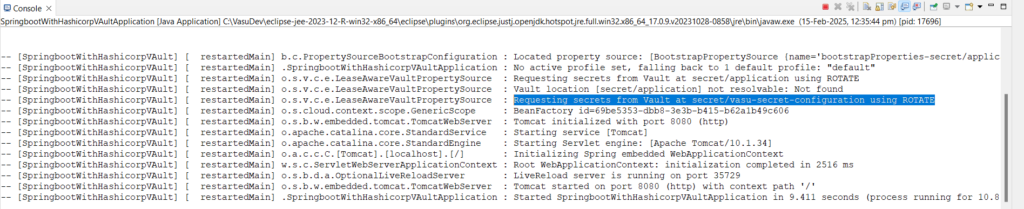
Code language: CSS (css)Now run your application and see the logs. And search for the string Requesting secrets from Vault at. This log tells that our application is requesting secrets from vault at our defined path.
Note: Above this highlighted logs you also seeing log saying Vault location [secret/application] not resolvable: Not found. This is because by default vault search for the secret inside the path same as our application name. So make sure you define this property spring.cloud.vault.kv.default-context and give the value of the path that you have created in bootstrap.properties file.
After application startup. Just call the API that we created to fetch username and password value from vault. In response you ‘ll see the same value that we set in vault.